Cyber crime
While the world is fixated on COVID-19, another pandemic is infecting us. This ‘virus’ is also new, complicated, and constantly evolving. It also destroys lives and causes major economic and social disruption. Like COVID, it will be with us for the foreseeable future. Unlike COVID, there is no comprehensive vaccine.
I am describing cyber-crime.
Recently, I have received many newsletters and read countless articles about cyber-crime. In CNN on 18th December: “Cybersecurity and Infrastructure Security Agency (CISA) has determined that this threat poses a grave risk to the Federal Government and state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations. The agency also acknowledged Thursday that the hackers used “tactics, techniques and procedures that have not yet been discovered.”

In its newsletter for December, the prestigious think tank ‘Foreign Affairs’ reiterates the serious attacks that have occurred in the USA. The authors write: “Washington has failed to devise a strategy to deter cyberattacks or to respond strongly enough when such attacks have occurred.” The same can be said of almost every government.
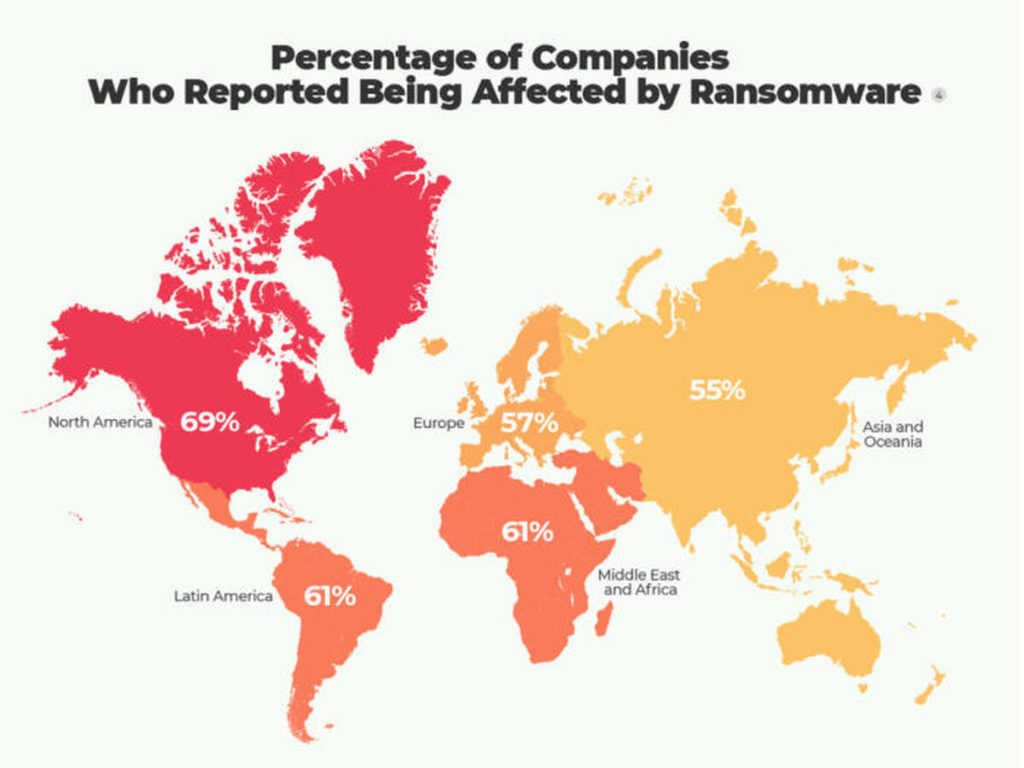
HSBC writes to its corporate customers:
One million UK cases of cybercrime were reported to Action Fraud (a UK police authority) last year alone. The 2016-17 joint National Cyber Security Centre & National Crime Agency report attributes 47.4% of all crime committed in the UK to cyber-enabled or cyber-dependent attacks.
The UK Financial Times on 19th December talks about the great hack attack; “How Solar Winds breach exposes big gaps in cyber security”. This refers to security breaches in a piece of third-party software used by many US agencies.
On a personal level, recently I found myself looking at ‘Settings’ in my wife’s Facebook account. I was appalled. Many aspects of our personal lives, our contacts, friends, addresses, emails, and phone numbers were available for anyone who chose to access them. Facebook allows you to limit access – but you must know how to do it. More importantly, you must want to. “It’s too much trouble,” is my wife’s response. “I’ve got nothing to hide.”
At a national level, security and society are threatened. At a corporate level, businesses are vulnerable to extortion. As individuals, we are open to blackmail, fraud, scams, and ransom demands.
What can we do?
Fortunately, like COVID, ‘medical’ help is to hand. Like COVID too, we all must take our own precautions. Governments do what they need to do. Businesses face risks of all kinds anyway; they must now protect themselves against cyber threats also.
Individuals owe it to themselves, the companies for which they work, and their families to take sensible precautions.
Primary Access, a network connecting entrepreneurs, recently published an authoritative and useful report. Here are some facts:
- 86% of all data breaches were for financial motives
- only 5% of folders in corporate networks were judged to be adequately protected
- 80% of data breaches can be attributed to poor password hygiene
- Post-2019, at least 43% of cyberattacks were made on small businesses.
2020 has seen a severe rise in attacks on businesses and establishments involving ransomware. This is malware that encrypts (usually sensitive) files on targeted systems. The criminals then demand money in return for decryption or not leaking sensitive data.

An easy and common way to install malware is to discover and appropriate users’ passwords. Cybersecurity professionals point out that workers themselves can prevent most cyber disruptions. Using common sense about basic procedures like passwords would prevent 80% of all attacks. For example, of the 200 most used passwords, 2.5m people were using the absurd ‘123456’. This alone led to over 2.3m data breaches.
In this year of remote-working, most workers are using their own, ad hoc, cybersecurity methods – or often none – on their own computers/phones/tablets. Over half of corporate security officers in one poll reported even being unable to know the exact number of devices connected to their company networks.
We worry about the effects of COVID-19 on humanity. But how much more are we dependent for modern existence on computer systems? In his 1955 novel ‘The Chrysalids’, John Wyndham envisaged a formerly advanced society reduced to neo-religious dictatorship because of their forebears ‘sins’. A technological catastrophe had occurred that reduced the survivors to Neolithic behaviours.
More recently, Robert Harris’s ‘The Second Sleep’ imagines a world where the internet has vanished. The novel is set in Britain 800 years from now, after a systemic collapse of technical civilisation. Into this “Dark Age” steps a rejuvenated and dogmatic church, whose authoritarian rule and obsessive suppression of heretical “scientism” ensure that people live in brutal and backward conditions.
These are works of fiction. Yet modern existence depends on technology and the software it needs to function. Technology dominates our lives – even those who ‘never use it.’ A nuclear war seems less threatening now than a society unable to function because technology no longer exists.
Conclusion
There are many groups at work in the world of cybersecurity. These include nations and businesses as well as criminals. The future is uncertain and will always be so. We should expect our politicians to take cybersecurity as seriously as they do the risks from pandemics and climatic change. We should demand that businesses protect themselves and are prepared.
Yet, as with COVID, each of us has personal responsibility to protect ourselves, those we love and those with whom we work. We cannot prevent every attack. But more tools are becoming available for normal users. Most are simple, well known, and easy to deploy.
If you have not already done so, please act – NOW.
Worked on the article:

Wanlikhang





